Here is the latest issue of the IoT Central Digest. This digest features stories about farming, security, applications and developers. Our community continues to grow and more members are contributing pieces for discussion and knowledge. If you're interested in being featured, we always welcome your contributions on all things IoT Infrastructure, IoT Application Development, IoT Data and IoT Security, and more. All members can post on IoT Central. Consider contributing today. Our guidelines are here.
Featured Posts (677)
A smart, highly optimized distributed neural network, based on Intel Edison "Receptive" Nodes
Training ‘complex multi-layer’ neural networks is referred to as deep-learning as these multi-layer neural architectures interpose many neural processing layers between the input data and the predicted output results – hence the use of the word deep in the deep-learning catchphrase.
While the training procedure of large scale network is computationally expensive, evaluating the resulting trained neural network is not, which explains why trained networks can be extremely valuable as they have the ability to very quickly perform complex, real-world pattern recognition tasks on a variety of low-power devices.
These trained networks can perform complex pattern recognition tasks for real-world applications ranging from real-time anomaly detection in Industrial IoT to energy performance optimization in complex industrial systems. The high-value, high accuracy recognition (sometimes better than human) trained models have the ability to be deployed nearly everywhere, which explains the recent resurgence in machine-learning, in particular in deep-learning neural networks.
These architectures can be efficiently implemented on Intel Edison modules to process information quickly and economically, especially in Industrial IoT application.
Our architectural model is based on a proprietary algorithm, called Hierarchical LSTM, able to capture and learn the internal dynamics of physical systems, simply observing the evolution of related time series.
To train efficiently the system, we implemented a greedy, layer based parameter optimization approach, so each device can train one layer at a time, and send the encoded feature to the upper level device, to learn higher levels of abstraction on signal dinamic.
Using Intel Edison as layers "core computing units", we can perform higher sampling rates and frequent retraining, near the system we are observing without the need of a complex cloud architecture, sending just a small amount of encoded data to the cloud.
With the global population expected to reach 9.7 billion people by 2050, innovation in the agricultural industry is more important than ever. This growth brings with it a need for increased food production and a dwindling availability of arable land. Projections show that feeding a population near 9 billion people would require raising global food production by some 70%. To provide for such steep demands, old farming techniques are simply no longer adequate. Thankfully, the agriculture industry is a burgeoning sector within the Internet of Things, and farmers globally are ready to reap the benefits.
Let’s look at a few ways IoT is helping the agriculture industry around the world.
-
Smart Ag Is Environmentally Friendly
Agriculture is responsible for a significant environmental footprint, accounting for 80% to 90% of US water consumption, releasing massive quantities of chemical pesticides, and producing more greenhouse gas emissions with animal agriculture alone than all combined transportation. IoT technology can maximize production capabilities and minimize required resources in order to reduce the industry’s environmental harm. Sensors can be implemented to test agricultural factors such as soil for moisture and nutrient levels to ensure resources are being used as efficiently as possible. This way water and pesticides can be reserved from unnecessary use and alternates can be implemented.
-
IoT Provides Precision Control for Farmers
The agriculture industry reaches far and wide, and each sector involves too much labor for one person to accomplish alone. As a result, much of the agriculture industry relies heavily on trusting intuition and human judgment. This also means that workers are nearly irreplaceable during illness or absence. Implementation of IoT technology can allow for real-time access to information that otherwise would take too much time or effort to obtain. Managers can have remotely controlled decision-making capabilities at their fingertips rather than having to wait for reports and then send out orders to workers. For example, rather than using valuable workers, drones are now available to monitor crops or apply treatment to specific areas. Also, companies like Lecia have developed GPS-guided combines and other agricultural IoT technologies. Aeris is helping to make solutions like these possible through cellular connectivity, perfect for remote real-time access to critical data.
-
Farms Are More Productive With IoT
As agricultural businesses gain more insight and control over their operations, they are able to make better business decisions and thus increase productivity. If a farm can use drones or sensors to monitor fields or cattle, for example, then the experience of the farmer can be utilized to make decisions while the manual labor previously needed to monitor these areas can be better repurposed elsewhere. IoT technology can also be applied to agricultural machinery, allowing for preventative maintenance and more accurate reports in the case of a malfunction, saving time and money. As smarter decisions are made regarding resources, productivity will improve.
-
Smart Farming Saves Money
According to the USDA, some of the top expenses of agricultural businesses include feed, labor, fuel, chemicals, and farm supplies and repairs, all expenditures that can be reduced with the help of IoT. Implementing IoT technology can allow businesses to make better decisions about efficiently using resources including assets, labor, and capital, significantly reducing operational costs. Replacing and improving past techniques will be the only way to maintain a competitive advantage with rising demands and ever-improving technology.
-
IoT Provides Transparency for Consumers
As more data is made available to the public, consumers demand high quality products more emphatically than ever. Concerns continue to emerge regarding the environmental footprint, personal health effects, and other details surrounding food production. Utilizing IoT technology in production is the only way to provide consumers with the data and transparency that is now the standard expectation, and thus maintain a competitive advantage in the industry.
When you’re ready to connect your agriculture devices to the Internet of Things, contact Aeris for a customized IoT solution.
Originally Posted by: Shawn Wasserman

Shodan search results show that over half a million devices use the 10-year-old OpenSSH 4.3 software. This puts all these devices at risk.
One doesn’t have to look too far to realize how vulnerable the Internet of Things (IoT) can be. It just takes a quick search on IoT search engines like BullGuard and Shodan.io.
During a presentation at PTC LiveWorx 2016, Rob Black, senior director of product management at PTC, outlined how black hat hackers could get into over half a million connected devices using an old software known as OpenSSH 4.3.
OpenSSH is a secure shell (SSH) protocol used to allow users access to networks from a remote location. It’s harmless, even useful, if used by the right user in a controlled way.
Unfortunately, a popular version of the software, OpenSSH 4.3, has been out for about a decade. As a result, it has developed a laundry list of vulnerabilities that hackers can use to gain access to systems.
According to the Shodan IoT device search engine, over half a million devices on the ‘net still use this outdated software.
“Half a million devices are on the open Internet with 10-year-old software that allows you to tunnel inside to their network. Who thinks that’s good?” Black rhetorically questioned. “This is one example. One search. One software. One version of a software. There are millions of exposed resources on the Internet.”
The scary thing is that Black explained that some search results will bring up IoT devices associated with power plants and wind tunnels. According to AdaptiveMobile, a mobile network security company, up to 80 percent of connected devices on the IoT do not have the security measures they need to protect us. Once you find a device on Shodan, you can see many characteristics on that device which will help hackers get into it.
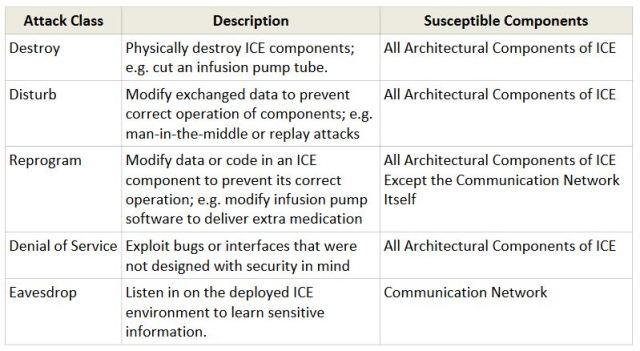
These attacks can even prove deadly depending on the IoT application. Take an integrated clinical environment (ICE) like an IoT-enabled hospital. Without proper security, many types of attacks have the potential to risk lives. According to a report published by the Industrial Internet Consortium, these attacks fall into five categories.
Engineers are designing these IoT devices, sensors and edge points. To ensure that hackers are kept at bay, these engineers need to understand and learn from their software engineer and IT cousins.
“From a design point of view, engineers need to learn about hacking security. You need security at the edge point to make an intelligent analytic device,” said Michael Wendenburg, CEO at Michael Wendendenburg Online Redaktion. “If you hack into that point, you hack into all this data. Engineers are not prepared for that.”
Black agreed, saying, “It’s our role as practitioners of IoT is to really manage those devices that we have in a smart way.”
How Do IoT and Cloud Security Differ?

Black explained that unlike in cloud security, humans may not be in the loop when it comes to IoT security. It’s not feasible for millions of users to be there to hit “Okay” to update software in billions of devices.
An engineer might think that as long as the cloud system utilized by the IoT device is secure, then all is well. However, there are differences between an IoT system and a cloud system.
Black explained that on the cloud, users and applications are both managed. There are security tools and permissions put into place. On the operations side, servers will be secured and ports will be closed and audited. This takes a lot of testing, but it’s been done before. IoT security, on the other hand, adds complexity.
“Cloud security has been around for a long time and there are lots of good strong practices and management around cloud applications. For IoT, the key difference is we connect things,” clarified Black. “A lot of the challenge is the number of devices to manage and the differences between these devices.”
“There are a bunch of new issues out there like rogue sensors and rogue data sources,” said Andy Rhodes, division head of IoT at Dell. “If you’re orchestrating a turbine or a damn and someone hacks into that and changes the settings, then there are catastrophic issues.”
Here are some other key differences between cloud and IoT applications:
- IoT has a stronger potential for damage as water mains can be shut off, power plants can become critical and cars made unresponsive on the road.
- IoT has a diverse number of devices, operating systems and protocols making it hard to consolidate and standardize as companies grow and products change.
- Human interactions with all the devices is not scalable. For instance, humans many not be there to hit “Okay” for an update.
The key is to work together. Engineers and IT professionals need to demolish their silos and learn from one another to make the IoT ecosystem secure. However, just because the IT crew has the ecosystem covered on the cloud doesn’t mean the devices and sensors are secure.
“IT [Information Technology] knows how to do security and a lot of this is still traditional IT security working alongside the OT [Operations Technology] people to understand how to secure the sensors as well,” described Rhodes. “You need [security on the device] and network security on the IT side because data flows two ways so you have to secure both ends of that spectrum.”
How to Manage Your Connected Device
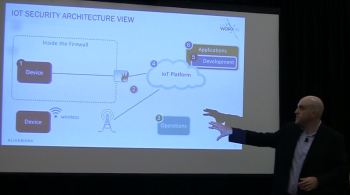
Black demonstrating an IoT security architecture.
With current IoT trends, if your device isn’t connected to the Internet, it soon will be. Otherwise, it will not keep up with the 30 billion other connected devices Gartner expects to see in the market by 2020.
So the question may not be whether to get into the IoT market given all the security risks. It should be a question of how to manage connected devices with all these security risks.
Black demonstrated what a simple IoT architecture might look like. It includes devices within a firewall, wireless devices outside the firewall and having those devices connecting into the IoT platform. Then, all of this will be used in an application that will use the data from the devices to perform a function. All of these systems, applications and development tools used to make the system must be made secure.
The issue is that because all of these different systems are under the control of various organizations on the vendor, customer and public levels, it can be confusing to establish who is really responsible for all of this IoT security.
“I argue that for IoT we have a shared security responsibility,” noted Black. “This is not a one-entity responsibility. It is shared between the providers of the infrastructure, service, platform, application and the end customers.”
Importance of User Roles on IoT Security
Given all of the organizations and users that might be associated with one IoT system, defining roles for these organizations and users is of high importance.
Each user and organization will have different roles, which will define levels of control over the IoT system. For instance, you don’t want to give your customers visibility into and control over all of the IoT devices on your ecosystem. This could make the data of your other customers insecure, as competitors might gain insights due to the information on your system and the lack of roles governing the system.
However, a maintenance team that services all the devices sent to customers will need to see which devices from each customer will be up for servicing.
The key takeaway is that as your system grows on the IoT, much of this role management should be automated. Otherwise, the role management will not scale with the IoT system if a human remains in the role assignment loop.
“From a visibility and permission standpoint, what you really want are mechanisms to drive that behavior,” instructed Black. “When new devices are added, if you have a manual process, that is not going to scale when you [have] tens of thousands of devices. You are going to need a system that drives this behavior automatically. You just need to set the rules beforehand to ensure the users are put in the right groups.”
Division of Systems is Key to a Secure IoT Ecosystem
The division of permissions shouldn’t just be between roles. It should also be between systems within the IoT device itself. Engineers must design some systems and subsystems to be independent and separate from all other systems. This will ensure that if a hacker compromises your device, they will not be able to take control of key systems.
After all, there is no reason for an entertainment system in a car to be linked to the steering, brakes and accelerator of a car. As the WIRED video below shows, though, this was the case with the Jeep Cherokee. As a result, hackers were able to mess with one reporter’s drive on the highway with hilarious outcomes—but the joke isn’t funny anymore if people actually get hurt.
“The way some of these systems are designed, if you have access to this you have access to multiple design elements in the car,” said Frank Antonysamy, head of engineering and manufacturing solutions at Cognizant. “The way we are dealing with this is to isolate as much as possible and then get the data.”
“When you look at it from a system design [perspective], in an automobile for example, there is still a fair amount of isolation written into the design,” said Antonysamy. “Because I have access to my control panel doesn’t mean I have access to the accelerator. That kind of design-based isolation is critical at least until we get a zero-vulnerability scenario.”
Eric van Gemeren, vice president of R&D at Flowserve, explained that the automobile industry and other IoT device creators can learn a lot from the process industry on the separation of systems within a design.
“In the process industry, it’s different from having a car that’s IoT-enabled and someone can hack into it,” said van Gemeren. “In the process industry, there are well-established IEC [International Electrotechnical Commission] and ISO [International Organization for Standardization] standards for safety and compliance. The control communication network is always separate and independent from the diagnostics and asset management network. It’s very clear that when you design that solution, there are certain features and functions that will never be available through wireless, in a discrete controlled domain, with an entirely different protocols and with robust security on top of it.”
“A lot of the stuff we are talking about in the IoT space is all about gathering outbound asset information,” added van Gemeren. “You can’t send back control information or directions that can hijack the device.”
In other words, van Gemeren explained that if a safety system like fire suspension sprinklers were installed in a process plant, they will need to be on an isolated system.
Do Your Devices Need to Talk to Other Devices?

Black explained the scenarios in which you need to use device-to-device
When people think about the IoT, many of them think of connected devices communicating with each other over the Internet.
Though there are situations when the data should be sent to the cloud, there are also situations where it is faster and more efficient for devices to talk to each other directly.
“You could go up to the cloud and negotiate up there and bring it back down but that is not using bandwidth efficiently and what happens if you lose network connectivity? Will your devices fail? Do you want them to be dependent on the network?” asked Black.
When connected device need to talk directly, you will need a way to authenticate the devices mutually as well as a method of authorizing the devices to an appropriate level of interactions.
“It doesn’t make sense for one car to have the authorization to turn on the windshield wipers for another car,” joked Black.
The Importance of Provisioning and Approval of an IoT Device
This brings us to another key step in setting up a secure IoT system: ensuring your processes can set up provisioning and approval for device-to-device communication, data ownership, de-provisioning and more.
“Any process that runs off of administration approval will fail on an IoT scale,” remarked Black. This is similar to the creation of roles the human needs to be out of the loop. Black added, “You can’t design a process based on admin approval—it might work for a hundred devices but it won’t work on a large-scale system.”
Unfortunately, you can’t just let all devices interconnect without a provisioning and approval process either. Take the Superfish scandal, for example. The program was intended to provide advertisers with a way to show ads based on a user’s Internet searches.
This sounds innocuous enough until you realize that, at the time, all Lenovo laptops had the same self-signed certification key for all the laptops that shipped out with the program. This allowed for man-in-the-middle hacking attacks that could intercept the Internet communications of any Lenovo laptop with the Superfish program still installed.
“Ensuring trust when you’re bootstrapping a device is challenging even big laptop manufacturers can make mistakes,” said Black. “We need to think through some of those processes to see how do we get secrets onto a device. You need a well-defined mechanism for establishing trust on your device.”
One method Black suggested to get your devices onto your IoT system with secure provisioning and approval is to use your enterprise resource planning (ERP) system. If your ERP system were connected to the IoT system, then the provisioning and approval process will expect to see the device. Not only would this system be secure, it can also be made scalable as there will be no need to have a human in the loop.
The Importance of De-Provisioning When You Re-Sell a Connected Device

Black explained the importance of factory resets and de-provisioning when selling used devices.
There is a lot of confidential information that can be stored on a connected device. Therefore, if users aren’t careful, they could be giving a hacker everything they need to get into the system when re-selling these devices.
The average user would know enough to delete their personal and business data from the device, but there still might be information on the re-sold device that can open doors to hackers.
For instance, the device might store digital keys that were used to encrypt the data you were sending and receiving from the Internet. If you were to sell that equipment without changing those keys, then whomever you sold that equipment to could now be able to decrypt all of the data you sent and received while operating the device. Assuming the hacker intercepted that data in full knowledge that you were to sell the equipment, they now have gathered a lot of information on your personal or business operations.
As a result, engineers should design easy to use de-provisioning procedures for the users of their devices.
Whose Data Is It Anyway? Where the Contract’s Made Up and Protection Should Matter.

Black asked the question: Whose data is it anyway?
One point of contention for the development of IoT security is the question of who owns the data.
Is it the device manufacturer, systems operator, device operator or the maintenance operator?
Will the answer be dependent on the IoT device application?
These questions need answers if robust security measures are to be put into place. Otherwise, the right information might end up in the wrong hands.
“We’ve seen a range of responses about data ownership and a lot revolves around privacy,” said Colm Pendergast, director of IoT technology at Analog Devices. “To a large extent, it will come down to negotiations between various partners in an ecosystem.”
“[Who owns the data] is a question that is always on the table,” said Chris May, account executive at ARIDEA SOLUTIONS. “It depends on the type of data being acquired. If it’s general weather data, then people are not very concerned. The weather is the weather… When you get to environmental data, it’s a completely different story. They are very protective of that data. [What] If the wrong person gets that data and they don’t understand how to interpret it? [What] if they can’t understand it’s a sensor being recalibrated and they think a water shed was contaminated? It would be massive lawsuits.”
It appears that though 54 percent of surveyed consumers might be comfortable sharing their data with companies, the reverse is not always true.
Alternatively, Black used an example of a medical device company. If the company is sold, then it makes sense for whomever buys the company to also own the data. After all, it will, in theory, be using said data to service the same clients. It isn’t in the client’s interest for the data to start at point zero.
However, does the answer of selling data ownership change with the scenario? What if, instead of a company being sold, it’s a house? Who owns all the data of the smart home—the previous tenants or the incoming tenants? It might be useful for the new tenants to know the power usage history of the house so they can budget their expenses, but do you want strangers to have data like that?
“When you think about how many different entities are involved with an IoT implementation, there are a lot of them,” said Black. “Some of them probably have rights to some of that data and some it’s probably better if they don’t have it.”
Before security walls are put up for an IoT device, these questions must be answered. Otherwise, an owner of the data might be cut off from their property. This can lead to some serious legal ramifications. On the other hand, not understanding where the line in the sand is for data can also open up security risks.
“If there was one single challenge that people are concerned about and has slowed IoT deployments is the question of security and integrating security solutions all over that technology stack. It is one of the bigger challenges,” said Pendergast.
However, one solutions to the IoT data question may not lie with the engineers, programmers or designers. It might be in the hands of public relations educating the public about IoT security and what data is and isn’t being collected.
“We deal with the medical device market and we constantly face the issue that we can’t send patient data—and we are a cloud-based platform, so that is a challenge,” said Puneet Pandit, CEO of Glassbeam. “We are not taking the patient data; we are taking the operation data. I think that is a constant question. There is a lot of education that has to be done in the industry to clarify what IoT data means at the end of the day. People have created security barriers for all the right reasons, but in the context of IoT you are taking machine and operational data and that isn’t something that is included on data privacy.”
Reducing IoT Attack Surfaces: Do You Need Access to the Open Web?
Shodan is only able to show the IoT devices that are on the open web. The number, as well as types, of devices that it can find is certainly scary.
“[Security is] still the top-two or -three concern of customers when you read surveys and speak to them,” said Rhodes. “What you’ve basically done is you’ve opened up a surface of attack either as a gateway or the things themselves.”
Does your device need to be on the open web? Do multiple surfaces of attack need to exist? The answer is no—not if engineers design the device to be the one to initiate communications.
“Different IoT solutions have the capability to perform device-initiated communication,” said Black. “That means that from a connection standpoint, if your device initiates communications, then that device is exclusively paired with one server on the cloud. That device is only going to communicate with that server.”
In other words, the device won’t be generally available on the Internet.
“It’s something to think about. Can I communicate with this device from every [access point] on the earth or is it tied to a single server? Because you are really reducing your attack surface with that kind of capability,” Black explained. “You reduce your attack surface so you are not worried about everything in the world. You are only connected to a very limited set of servers.”
If your device can connect to any endpoint on the Internet, then any hacker at any location could in theory send a command to that device. However, if the device is connected only to one server via a device-initiated communication, then only that server can send commands. The theory is that your server will be within internal IT infrastructures and securities.
However, there is a downside to device-initiated connectivity. You will have to rely on the device to connect to the system in order to initiate an update or collect data. In other words, you can lose connections to the device as soon as a customer changes firewall securities or the network is interrupted.
As a result, if engineers chooses to use device-initiated connections for an IoT system, then they will need to inform the customer. The customer will need to understand if the firewall and network connection isn’t interfering with the connection.
“We’ve seen a lot of software partners changing their architecture to support intermittent connectivity,” said Gerald Kleyn, director of engineering at Hewlett Packard Enterprise (HPE). “In some cases, if the weather gets bad and [satellite communication] goes down, then when it comes back up it starts releasing things that have been stored on the edge back up to the cloud.”
What to Do When You Find a Vulnerability on Your Connected Device
The longer your device is in the real world, the more likely it is that a vulnerability will be found. As a result, engineers will need to design software update compatibility into their devices.
“You need a software distribution mechanism that will work for all of your devices that’s scalable, secure, flexible and efficient,” said Black. “It needs to be flexible because all your devices are different, so they need different processes and procedures.”
“You need to be able to say, if the install isn’t going right, that you need to hold back and notify your system. You need to be able to say, ‘do this for North America first, or Europe or everyone but that customer that doesn’t want updates,’” added Black. “Without a plan, you will be sad when the next Heartbleed comes out. You are going to have to patch. So what is the mechanism you are going to utilize?”
This all must seem very complicated, but much of this IoT security issues will be answered when you choose the IoT platform to run, manage design the system. Black says that when choosing your IoT platform, keep these three main security challenges in mind:
- Managing the complex interactions between devices and user
- Patching security updates to your devices in an easy and secure fashion
- Reducing the risk by mitigating cyber-attacks form finding your device
You can view the original post Here
In a new update to the Worldwide Semiannual Internet of Things Spending Guide, the International Data Corporation (IDC) forecasts that U.S. organizations will invest more than $232 billion in Internet of Things (IoT) hardware, software, services, and connectivity this year. And IDC expects U.S. IoT revenues will experience a compound annual growth rate (CAGR) of 16.1% over the 2015-2019 forecast period, reaching more than $357 billion in 2019.
The industries leading the way in U.S. IoT investments are Manufacturing and Transportation at $35.5 billion and $24.9 billion, respectively, in 2016. However, Cross-Industry investment, which represents use cases common to all industries, will approach $31 billion this year. The IoT use cases receiving the greatest levels of investment from U.S. organizations across these three industry segments are:
- Manufacturing Operations, which supports digitally-executed manufacturing, or how manufacturers use intelligent and interconnected I/O (input output) tools – e.g. sensors, actuators, drives, vision/video equipment etc. – to enable the different components in the manufacturing field – e.g. machine tools, robots, conveyor belts etc.– to autonomously exchange information, trigger actions and control each other independently.
- Freight Monitoring, which uses radio frequency identification (RFID), global positioning system (GPS), GPRS, and GIS technologies to create an intelligent, Internet-connected transportation system. This system carries out the intelligent recognition, location, tracking and monitoring of freight and cargo through exchanging information and real-time communications via wireless, satellite or other channels.
- Smart Buildings, which utilize advanced automation and integration to measure, monitor, control, and optimize building operations and maintenance. The key concept is optimization – meaning the deployment of a set of integrated control systems capable of adapting in real time to both internal policies and external signals. These systems manage how building equipment operates to use energy in the most efficient and cost-effective way.
Looking across all U.S. industries, these three IoT use cases will receive the greatest levels of investment throughout IDC's forecast. The next three largest IoT use cases in terms of U.S. revenue will be Remote Health Management, Smart Grid (Electricity), and Smart Home. The IoT use cases that will experience the greatest revenue growth in the U.S. over the 2015-2019 forecast period are In-Store Contextualized Marketing, Connected Vehicles, and Insurance Telematics.
"A use case represents a detailed composition of a technology investment that is made to produce a set of end user benefits," said Marcus Torchia, research manager, IoT for IDC's Customer Insights and Analysisteam. "The long term opportunity for IoT vendors is helping to identify and create immediate and residual benefits for end users through their technologies. We see strong opportunities across many industries. For example, in highly instrumented verticals like manufacturing and transportation, large data sets are used to optimize operational processes and extend the life of high capital cost assets. In other sectors like healthcare and consumer, IoT technology is being used to produce benefits that improve quality of life."
While Manufacturing and Transportation will lead the U.S. in terms of overall IoT investments, the Insurance, Retail, and Healthcare industries will see IoT spending levels increasing by 135%, 101%, and 96%, respectively, over the forecast period. In addition to driving some of the largest IoT investments, the Cross Industry segment will also see revenue growth of more than 100% through 2019.
Guest post by Jules Oudmans. This article first appeared here.
An important, crucial, aspect in IIoT applications is the communication layer. This layer is responsible for relaying sensor values from the field to northbound processing of this data and the southbound control.
In my previous blog I concluded that IIoT is reality, but headaches are ahead choosing the right protocol and communications provider, especially when your IIoT solution requires long-range support, will be deployed in multiple countries and needs cross border coverage.
Protocols, protocols, protocols …
The myriad of protocols in IoT land is still growing and can truly be overwhelming. In below table I have limited the protocols listed to only those that support long-range. Next to this the table shows data rates and bi-directional capability, these are important qualifiers for typical IIoT solutions and may help you choose the right protocol … but continue reading!!

What Protocol … No Sorry What Provider .. or Protocol !??
The vast majority of today’s M2M communication relies on 2G and 3G networks. These networks reliably provide, relatively low-cost, long range and border stretching networks for IIoT applications. They are offered by a wide variety of providers and support roaming. A truly excellent choice for your IIoT solution … were it not that 2G/3G networks are expected to disappear in the next 5 years. This is where the headache starts ... as today no cross-border roaming IIoT provider is out there supporting a protocol with an expected useful lifetime equal to a smartphone.
You could off course develop your IIoT solution – sensors, middleware, processing nodes et cetera. – to support multiple protocols but this is unpractical and costly.
When we limit ourselves to an IIoT deployment that requires long range connectivity, is low- cost, will be deployed in multiple countries and will be available after 2020 than, today, we can choose between:
- SigFox: A protocol with country coverage in certain EU countries and countries under rollout such as Brazil, Germany, UK and the US; and
- LoRa: A protocol offered by multiple providers. Some country covering networks are available today and some network providers cover regions or cities.
SigFox
SigFox is available in countries where rollout is requested (chicken and egg). Today roaming is not supported, but besides this all data goes over SigFox managed servers(!). The latter something that certain companies will not want.
LoRaWAN
LoRaWAN is growing in popularity, LoRa networks are predominantly rolled out by the NTCs – National Telephone Companies – but you also see new communication providers popping up such as DIGIMONDO in Germany, Wireless Things in Belgium et cetera. This because there are no frequency auctions for LoRa. So far so good, but LoRa also has a small caveat: roaming is under development – expected this year.
Conclusion
With new communication providers popping up out of nowhere and NTCs pushing rollouts of LoRa like there is no tomorrow there is a lot of turbulence in the IIoT communications space.
Today no cross-border roaming IIoT provider is out there supporting a protocol with a ‘long’ lifespan. Today LoRa is, in Europe, one of the best alternatives to focus on.
Closing Notes
In this post I have not taken LTE-M into consideration as it is becoming available this year(1):

LTE-M rollout will likely be fast as it can utilize existing mobile phone infrastructures. I recommend you to read the Ericsson White Paper: Cellular networks for massive IoTand to keep an eye on this space. But also don’t lose track on Ingenu (promising(2)),NWAVE and NB-IoT. Some expect that NB-IoT will ‘crush’ LoRa and SigFox(3) .. just furthering the headache.
Weightless was left out of the consideration in this article as it is only available in a few different European cities and is more mid than long range .. but hey it may well suite your IIoT needs!
Due to the turbulence and changes in communications land this article very likely needs to be revisited in 3-to-6 months from now.
Finally: If you are looking to set-up a private LoRaWAN network, or wanting to play around with LoRa possibilities there is not much stopping you. For approximately 280$ you can have your own LoRa network – have a look at TheThingsNetwork.
UREASON
UREASON has been at the forefront of IoT /IoE, reasoning over real-time streaming data and events in the manufacturing industry and telecom. We apply an ensemble of techniques – best fitting the requirements – and a wealth of knowledge focused on providing a tailored response to the environment of our customers.
Our capabilities in the Industrial Internet of Things field include:
- Feasibility studies and Proof of Concepts including hardware prototyping and field tests;
- Support and roll-out of IIoT solutions in Operational Safety and Predictive Maintenance;
- Recommendations for human-cyber physical systems, augmented reality and Internet of Things technologies; and
- Support in Machine Learning and Big-Data initiatives supporting IIoT applications.
References
(1): Cellular IoT alphabet soup, Ericsson Research Blog, 2016
(2): RPMA Technology for the Internet of Things, Ingenu
(3): Vodafone to 'Crush' LoRa, Sigfox With NB-IoT, 2016
Development for the Internet of Things has grown substantially over the past 12 months according to the newly released Global Developer Population and Demographics Study from Evans Data Corp.
The number of developers currently working on IoT applications has increased 34% since last year to just over 6.2 million today. In addition, the increase of development for mobile devices, up 14% since last year, has led to smartphones being the most commonly connected IoT platform.
The study, which combines the industry’s most exhaustive developer population model with the results of Evans Data’s biannual Global Development Survey also provides fresh population data for the four major regions: North America, APAC, EMEA, and Latin America and for more than 40 countries. Population numbers for adoption of the hottest tech areas are also included.
“We're seeing how in the space of just a year, the possibilities introduced by the Internet of Things has attracted many developers.” said Michael Rasalan, Director of Research for Evans Data Corp.“This transition to IoT, while not without barriers, is rapid, because developers are able to leverage existing knowledge and expertise in complementary technologies like cloud and mobile, to create entirely new use cases. We're also seeing developers branch out from concepts centered on wearables to applications for more complex tasks, seen in the industrial space.”
For the general developer population, estimates and projections for growth to 2021 show APAC leading the pack with nine hundred thousand more developers than EMEA. Growth in India and China are predicted to keep APAC’s population the highest globally for the next several years.
The full report can be found here.
Original Post from: Vulpoid
Unmanned Aerial Vehicles (UAVs) offer new perspectives, both from a civilian and a military standpoint; yet, they present vulnerabilities having the potential to lead to disastrous consequences regarding public safety if exploited successfully, as evidenced by recent hacks. These repercussions can be prevented by implementing best practices, continuously assessing the technologies used and most importantly by remaining aware of the environment, of the weaknesses that may be exploited and of the threats that may emerge. The purpose of this article is not to provide countermeasures or solutions, but to outline flaws and vulnerabilities to better understand and address potential threats and threat actors.

Figure 1 UAVs hacks disclosure timeline
As shown by recent hacks, several professional Unmanned Aerial Vehicles (UAV) used byarmed forces, governments, police departments and the private sector are vulnerable to critical attacks which exploit both technical vulnerabilities and design flaws. This can lead to UAVs being spied on, made inoperable or controlled by the attacker unbeknownst to the UAV’s owner.

Figure 2 Drone’s ecosystem vulnerabilities

Figure 3 Operation Anarchist base location
From a military intelligence perspective, it’s a godsend to gather valuable information. The GCHQ/NSA joint Operation Anarchist[1] during which Israeli drones’ scrambled video signals were intercepted and reconstructed, providing the US and UK a clear view of Israeli drones’ position, movements, payload and video footage is the perfect example. The Operation Anarchist – which started in 1998, lasted more than a decade and was disclosed only in late December 2015 – was run from the Troodos Mountains, Cyprus, from where encrypted video signals between Israeli drones and their bases were intercepted and unscrambled using open-source software tools.
The obvious drawback however for governments is that the same techniques can be used against them and become a serious threat, particularly when it comes to State security and notably for law enforcement agencies. While entry-level drones present vulnerabilities, their main purpose seems to be to reduce cost. IBM researcher Nils Rodday proved that high-end drones were also vulnerable when he studied professional quadcopters used by law enforcement agencies in the context of his Master’s Thesis[2] in 2015. He showcased the results of the hacks during the RSA Conference 2016[3]. He also analyzed the quadcopters and discovered that the on-board chips lacked encryption implementation[4] which allowed him to hijack the drone by emulating the commands sent to the UAV through the controlling application. Furthermore, he took advantage of the weak encryption (WEP) used to cipher the link between the drone and its controller.

Figure 4 Drone flow architecture, by Nils Rodday, used in his work
In addition, concerns regarding homeland security have emerged, as shown by the case of the Mexican drug cartel who, in late December 2015, managed to control the US Customs and Border Patrol (CBP) drones’ movements[5]. This allowed the cartel to reroute the US CBP’s drones and to illegally cross the US-Mexican border, enabling them to smuggle drugs and people without being detected. The cartel used GPS jamming and GPS spoofing techniques which respectively disrupted the Command and Control (C&C) link, preventing the drone from receiving GPS signals, overriding legitimate ones and replacing them with fake ones, thus making it deviate from its original route.

Figure 5 GPS jamming / GPS spoofing

Figure 6 IDF Drones System hack
Moreover, warfare methods continually evolve and actors integrate new technologies in their arsenal, leveraging on them during actual conflict as evidenced by the recent hack of the Israeli Defense Forces’[6] (IDF) drone surveillance system. The hack was perpetrated by a member of the Islamic State who gained access to HD footage from IDF’s drones hovering above the Gaza Strip for at least 2 years, starting in 2012 but potentially up until the arrest in February 2016. As a matter of fact, using only commonly available tools such as a satellite dish and a radio receiver[7], the hacker was able to intercept IDF’s drones’ video streams and managed to decode them, thus providing the Islamic State with a clear view of IDF’s drones video footage.
As evidenced by the aforementioned examples, attacks take place in several heterogeneous contexts and originate from actors belonging to different domains and with different levels of skill. In all the above mentioned cases, these events highlight weaknesses and vulnerabilities in the technologies used by UAVs along with flaws in the processes that were put in place by the victims regarding information handling. Military, law enforcement and governments are critical targets; however, the private sector is not spared as drones are being considered more widely by corporations for new services – Amazon Prime Air is a great example of that and may result in very annoying hacking opportunities to say the least. Consequences may be a matter of national security and public safety, therefore implementing best practices, setting up proper countermeasures – such as spread spectrum modulation in the case of signal jamming – and using state-of-the-art technologies proves itself crucial, yet being aware of the threat landscape one’s facing along with one’s own kill-chain is fundamental in order to avoid and mitigate such cases at best.
View the original post by clicking: Here
Originally Posted by: Mimi Spier
The Internet of Things (IoT) is here to stay—and rapidly evolving. As we try to make sense of IoT’s impact on our lives and businesses, we also continue grappling with the security challenges.
As the IoT security landscape evolves, here are five key insights for designing and implementing IoT deployments for your enterprise.
1. Protect Your People
IoT has opened up a world of possibilities in business, but it has also opened up a host of ways to potentially harm employees and customers. A security breach is not limited to stealing credit card data, anymore. Anyone with the right access could breach firewalls or steal health records. A key challenge of the IoT world is providing the right access to the right people at the right time.
[Related: 5 Real Ways to Enable IoT Success in Your Enterprise]
2. Watch Your Things
As millions of “things” start joining the enterprise network, it also expands the surface area for hackers to breach your system. All these devices will be leveraging public Wi-Fi, cloud, Bluetooth networks, etc., which will create multiple points of vulnerabilities. Your system needs to be designed for security from the bottom up to account for:
A) Device level: better quality devices
B) Data level: encryption and cryptology
C) Network level: certificates and firewalls
D) Application level: login/authorized access
3. Poor Quality of Things
The standards for IoT hardware and software are still evolving, which means until we have any established guidelines, we need to account for a vast range in the quality of “things.” Some of these may be very sophisticated and hardy, while others may be of the cheap disposable variety. Which devices you pick may depend upon factors like cost, usage and the use case itself. However, be warned that lower-quality devices have been used to gain entry to a secure network.
“By 2020, more than 25% of identified attacks in enterprises will involve the Internet of Things (IoT), although the IoT will account for less than 10% of the IT security budget.” Gartner
4. Is Your Network Ready?
One of the biggest challenge for any IT department implementing company-wide IoT projects will be assessing and managing bandwidth. As millions of devices join your network at increasing rates, scaling your network’s bandwidth will be an ongoing struggle. Your bandwidth needs must remain elastic, so you can support your enterprise needs, while minimizing costs. It is critical to minimize exposure of your networks by using, for example, micro-segmentation.
5. Data Is Your Friend
As with protecting any system, predictive maintenance is the way to stay a step ahead of breaches. The usual ways of pushing out timely security patches and software upgrades will continue to be helpful. However, one big advantage of IoT is the sheer amount of data it generates. You can track operational data to create alerts based on anomalies in the system. For example, if someone logs into the system from Atlanta and then, 30 minutes later, logs in again from Palo Alto, the system should raise a red flag.
You can view the original post by clicking Here.
Guest post by Ruud Wetzels. This article originally appeared here.
This is a bold claim perhaps, certainly as it is made by a data scientist with no particular knowledge of machines, trains or planes, or any experience in running a factory. Yet I am convinced that in your data we can find clues for improving your maintenance process, be it in the form of improved up-time, reduced costs or extended operational lifetime of your equipment. The reason I'm confident is that nowadays the power of computers to find patterns and correlations in vast amounts of data far exceeds the ability of any human to detect such clues.
Killer-app
The technique is called predictive maintenance, and it has been named the killer-app of the Internet of Things. I could agree to that. Predictive maintenance is about something tangible and familiar from everyday practice, it's relatively easy to start with without a need for significant investments up-front, and the results become evident fairly quickly. In other words: predictive maintenance has the potential to quickly yield real benefits, both operational and financial.
It all starts with data
As most machines and equipment in use today are fitted with sensors that gather data, there is usually an abundance of data to work with. Even if this sensory data is not yet collected for maintenance purposes, often the amount of data that is available - say in maintenance logbooks or financial databases - is sufficient to get started. And of course external data about anything that might be relevant can be included, weather data for instance.
The art of data analytics
The next steps with predictive maintenance are to feed all available data into a model and identify the appropriate algorithms to analyze those data with. This choice of algorithms by the way is really what constitutes the art of data analytics, it is the very step that determines the quality of the results. These algorithms then turn all those data into a single number: the probability that a certain event - in the context of maintenance: a failure or a breakdown - will happen within a future time slot, say the next 72 hours. Provided that the input data is cleaned-up and ready for use, such a model could be up and running in a matter of weeks.
Making tradeoffs
What remains to be done is to establish a threshold for intervention: at what probability level of failure will you intervene and perform the appropriate maintenance activity? This is how the maintenance process can be tailored to specific business objectives, which in my view is one of the major benefits that predictive maintenance offers. It allows railway companies and airlines for example to make an explicit trade-off between customer satisfaction (i.e. run on schedule) and safety (i.e. accept delays in case predictive maintenance is warranted), a trade-off that will probably be different in both cases.
A leap of faith or an evidence-backed claim?
At this point the maintenance process has in effect been formalized. It is no longer run based on experience, intuition or a fixed set of instructions. Instead it is governed by an algorithm that produces a single number. To many companies, this is a somewhat scary thought, at least initially. Whether companies are willing to adopt such a formalized process depends to a large extent on human factors: how much affinity and understanding do management and maintenance engineers have of data analytics and what it can accomplish? In case the step to predictive maintenance requires too big a leap of faith, it can be run in parallel to the traditional maintenance process for some time, without making any interventions based upon its predictions. This way companies can gather enough evidence that I'm confident will back up my claim: predictive maintenance is the superior way of doing maintenance.
Photo courtesy of Teruhide Tomori
By Ben Dickson. This article originally appeared here.
The huge benefit that the Internet of Things (IoT) brings to different industries and domains is driving its growth and adoption at an unrelenting pace. Soon billions of connected devices will be spread across smart homes and cities, harvesting data, sending it to huge repositories for analysis and processing, and carrying out commands sent from smart apps and machine-learning-based systems.
While larger numbers of smart devices will unlock bigger opportunities for efficiency, energy and cost saving and revenue increase, they’ll also trail along some serious challenges and difficulties, some which are notably not addressable with current technological and communication infrastructure.
What’s wrong with centralized communications?
As is, all IoT ecosystems depend on client/server communications, centralized trust brokers and protocols such as SSL/TLS or mechanisms such as the Public Key Infrastructure (PKI) to identify network nodes and control communications.
These technologies have proven their worth for communications between generic computing devices for years, and will continue to respond to the needs of small, closed IoT ecosystems, like smart homes. But with the growth of IoT, centralized networks will soon become the bottleneck and cause lags and failures in critical exchanges because of too much network traffic, to say nothing of the extra investment they’ll require in terms of hubs and communications hardware. Imagine what would happen if your smart defibrillator failed to receive a command because your dishwasher, toaster, fridge, kettle and lights are having a nice M2M chat and have clogged up the network.
Decentralizing IoT networks
A solution would be to decentralize IoT networks in order to improve speed and connectivity. In many cases, substituting over-the-internet connectivity for local communication between devices will help increase speed and efficiency. After all why should a command exchange between a smartphone and light-switch have to go through the internet?
However achieving decentralization will present its own set of challenges, namely in the realm of security. And we know that IoT security is much more than just about protecting sensitive data. How do you make ensure security in communications between devices?
Devices would have to be able to communicate in a peer-to-peer manner and ensure security and integrity without the intervention of or dependence on a centralized trust center. The proposed system would have to protect the network and ecosystem against device spoofing and man-in-the-middle (MittM) attacks and make sure each command and message that is exchanged between nodes in a network are coming from a trusted and authenticated source and received by the right recipient.
How blockchain addresses the problem
Fortunately, the decentralization problem has already been solved in another popular technology: Bitcoin. The famous cryptocurrency is powered by a less-known (but no less exciting) technology named blockchain. The blockchain is a data structure that allows the creation and maintenance of a transaction ledger which is shared among the nodes of a distributed network. Blockchain uses cryptography to allow participants to manipulate the ledger without going through a central authority.
The decentralized, secure and trustless nature of the blockchain make it an ideal technology to power communication among nodes in IoT networks. And it is already being embraced by some of the leading brands in enterprise IoT technologies. Samsung and IBM announced their blockchain-based IoT platform called ADEPT at the Consumer Electronics Show (CES) last year.
When adapted to IoT, the blockchain will use the same mechanism used in financial Bitcoin transactions to establish an immutable record of smart devices and exchanges between them. This will enable autonomous smart devices to directly communicate and verify the validity of transactions without the need for a centralized authority. Devices become registered in blockchains once they enter IoT networks, after which they can process transactions.
There are many use cases for blockchain-based communications. A paper published by IBM and Samsung describes how blockchain can enable a washing machine to become a “semi-autonomous device capable of managing its own consumables supply, performing self-service and maintenance, and even negotiating with other peer devices both in the home and outside to optimize its environment.”
Other IoT domains can benefit from blockchain technology. For instance, an irrigation system can leverage the blockchain to control the flow of water based on direct input it receives from sensors reporting the conditions of the crops. Oil platforms can similarly use the technology to enable communications between smart devices and adjust functionality based on weather conditions.
What are the challenges?
In spite of all its benefits, the blockchain model is not without its flaws and shortcomings. The Bitcoin crew itself is suffering from inner feuds over how to deal with scalability issues pertaining to the Blockchain, which are casting a shadow over the future of the cryptocurrency.
There are also concerns about the processing power required to perform encryption for all the objects involved in a blockchain-based ecosystem. IoT ecosystems are very diverse. In contrast to generic computing networks, IoT networks are comprised of devices that have very different computing capabilities, and not all of them will be capable to run the same encryption algorithms at the desired speed.
Storage too will be a hurdle. Blockchain eliminates the need for a central server to store transactions and device IDs, but the ledger has to be stored on the nodes themselves. And the ledger will increase in size as time passes. That is beyond the capabilities of a wide range of smart devices such as sensors, which have very low storage capacity.
Other challenges are involved, including how the combination of IoT and blockchain technology will affect the marketing and sales efforts of manufacturers.
It’s still too early to say that blockchain will revolutionize and conquer the IoT industry. But it sure looks like a promising offer especially if its challenges can be met. We’ll see more of this in the coming months and years, as IoT continues to grow and become more and more ingrained in our lives.
Here is the latest issue of the IoTC Digest. Our community continues to grow and more members are contributing pieces for discussion and knowledge. If you're interested in being featured, we always welcome your contributions on all things IoT Infrastructure, IoT Application Development, IoT Data and IoT Security, and more. All members can post on IoT Central. Consider contributing today. Our guidelines are here.
Featured Articles
 Internet of Things Checklist: 4 IoT Prerequisites
Internet of Things Checklist: 4 IoT Prerequisites
Posted by Marcus Jensen
The application of the internet has moved past the cyber world and is spilling into the physical realm. Internet of things (IoT) is transforming everyday man-made landscape and making it smarter: from health care and home automation to public transportation and factory operations, humans are breaking new ground at a staggering rate.
Security-First Design for IoT Devices
Posted by Bill Graham
The Stuxnet malware was a wake-up call for embedded device security when it became public knowledge in 2010. Its sophistication and purpose made it clear that industrial control systems and the embedded systems used to control and monitor critical infrastructure were at risk. Machine to Machine (M2M) and Internet of Things (IoT) realities mean that more and more devices are being deployed and connected to each other. This connectivity is both the promise of IoT (data gathering, intelligent control, analytics, etc.) and its Achilles’ heel. With ubiquitous connectivity comes security threats - the reason security has received such a high profile in recent discussions of IoT.
Smarthome Security Concerns: The Question of Privacy
Posted by Nate Vickery
Today, we are building Smart homes. Our home appliances, our home security systems, our ACs, and not to mention our media sources – they are all connected and monitored via our smartphones, tablets and smartwatches. But when all of our technical devices, our homes, and finally our lives become completely automated – how are we going to maintain a safe environment? How are we going to protect our privacy? And what is the real price of conform? Let’s examine some of the Smarthome security concerns that you should be aware of, if you value your privacy.
Sensory Overload: Digesting Data From The IoT
Posted by Amy Krishnamohan
Have heard about the magic pill? Not sure how it works, but it helps you lose 20 pounds in a week while consuming the same calories as before. And you’ve probably also heard about the scary side effects of that pill. The need for magic pills is appearing in the IoT market as well. Thanks to the explosion of sensors to measure everything imaginable within the Internet of Things, enterprises are confronted with a never-ending buffet of tempting data.
The Top 50 IoT People to Follow on Twitter
Posted by David Oro
I recently shared the Top 10 Books to Read Now on IoT. In an attempt to keep everyone smarter and share resources in the most simple way, I created the ever ubiquitous listicle by compiling what I believe are the Top 50 IoT people to follow on Twitter. These are, as far as I can tell, real people and not brands.
Additional Links
Follow us on Twitter | Join our LinkedIn group | Members Only | For Bloggers | Subscribe
Original article is published at Forbes: link
Have heard about the magic pill? Not sure how it works, but it helps you lose 20 pounds in a week while consuming the same calories as before. And you’ve probably also heard about the scary side effects of that pill. The need for magic pills is appearing in the IoT market as well. Thanks to the explosion of sensors to measure everything imaginable within the Internet of Things, enterprises are confronted with a never-ending buffet of tempting data.
Typically data has been consumed like food: first it is grown, harvested, and prepared. Then this enjoyable meal is ingested into a data warehouse and digested through analytics. Finally we extract the nutritional value and put it to work to improve some part of our operations. Enterprises have evolved to consume data from CRM, ERP, and even the Web that is high in signal nutrition in this genteel, managed manner from which they can project trends or derive useful BI.

The IoT and its superabundance of sensors completely changes that paradigm and we need to give serious consideration to our data dietary habits if we want to succeed in this new data food chain. Rather than being served nicely prepared data meals, sensor data is the equivalent of opening your mouth in front of some kind of cartoon food fire hose. Data comes in real-time, completely raw, and in such sustained volume that all you can do is keep stuffing it down.
And, as you would expect, your digestion will be compromised. You won’t benefit from that overload of raw IoT data. In fact, we’ll need to change our internal plumbing, our data pipelines, to get the full nutritional benefit of IoT sensor data.
That will require work, but if you can process the data and extract the value, that’s where the real power comes in. In fact, you can attain something like superpowers. You can have the eyesight of eagles (self-driving cars), the sonar wave perception of dolphins (for detecting objects in the water), and the night vision of owls (for surveillance cameras).If we can digest all this sensor data and use it in creative ways, the potential is enormous. But how can we adapt to handle this sort of data? Doing so demands a new infrastructure with massive storage, real-time ingestion, and multi-genre analytics.
If we can digest all this sensor data and use it in creative ways, the potential is enormous. But how can we adapt to handle this sort of data? Doing so demands a new infrastructure with massive storage, real-time ingestion, and multi-genre analytics.
Massive storage. More than five years ago, Stephen Brobst predicted that the volume of sensor data would soon crush the amount of unstructured data generated by social media(remember when that seemed like a lot?). Sensor data demands extreme scalability.
Real-time ingestion. The infrastructure needs to be able to ingest raw data and determine moment by moment where to land it. Some data demands immediate reaction and should move into memory. Other data is needed in the data warehouse for operational reporting and analytics. Still other data will add benefit as part of a greater aggregation using Hadoop. Instant decisions will help parse where cloud resources are appropriate versus other assets.
Multi-genre analytics. When you have data that you’ve never seen before, you need to transform data and apply different types of algorithms. Some may require advanced analytics and some may just require a standard deviation. Multi-genre analytics allows you to apply multiple analytics models in various forms so that you can quickly discern the value of the data.
The self-driving car is a helpful metaphor. I’ve heard estimates that each vehicle has 60,000 sensors generating terabytes of data per hour. Consider the variety of that data. Data for obstacle detection requires millisecond response and must be recognized as such if it is to be useful. A sensor on the battery to predict replacement requires aggregation to predict a trend over time and does not require real-time responsiveness. Nevertheless both types of data are being created constantly and must be directed appropriately based on the use case.
How does this work at scale? Consider video games. Real-time data is critical to everything from in game advertising, which depends on near instant delivery of the right ad at a contextually appropriate moment, to recommendations and game features that are critical to the user experience and which are highly specific to moments within the game. At the same time, analyzing patterns at scale is critical to understanding and controlling churn and appeal. This is a lot of data to parse on the fly in order to operate effectively.
From a data perspective, we’re going to need a new digestive system if we are to make the most of the data coming in from the IoT. We’ll need vision and creativity as well. It’s an exciting time to be in analytics.
Wearable technology is a type of device that is worn by a user and often includes tracking information related to their health and fitness which it can then upload to the cloud. Other wearable tech includes devices that have motion sensors and cameras to take photos and sync with your mobile devices. Wearable devices can be quite useful, but they may present a huge danger to your privacy.
So far, the market has consisted mainly of early adopter businesses assessing the technology. This large group includes Tesco, which gave armbands to workers at a distribution center in Ireland to track products, allocate jobs and measure movement within the complex, with the goal of improving efficiency and accuracy. And health insurer 'Pru Health' offers a 'Fitbug' health and fitness device to their members as a part of it's 'Vitality' program.
It seems inevitable that in the next few years more businesses will begin to explore the potential commercial uses of wearable devices or even begin offering them to their employees, business partners or consumers. In addition, the next few years will no doubt see many employees bringing their own wearable technology into the workplace, for many reasons, such as health benefits and improving productivity.
A key danger for the wearable device market is that a large amount of personal data could be collected from most of these devices. Health and fitness devices could capture extremely sensitive details about a user’s health, and then send it automatically to the cloud for processing by the vendor, who then share it with third parties for 'big data' profiling and targeted advertising.
The 'big data' example really highlights the lack of current regulation for wearable devices and gadgets. Although the analytics and profiling might benefit some of those involved, including in some cases the user, it will become difficult for consumers to keep track of how much of their private data is shared by corporations, and where it's stored. And while many users may be ready to trade their data and lose control over it in exchange for some perceived benefits. Cloud Security is another major concern, and if breached, much of your personal data could be stolen or released.
Your data's security is a very important issue. Cloud Security has been breached numerous times in the past, and If exploited, wearable devices can expose a large amount of very intimate and extensive personal data about a user, including their health, current location, and their behavior. This of course already happens with smartphones, tablets and laptops, but the scale and intrusiveness of data breaches involving wearable devices could be unprecedented.
In the long term, there are data protection reforms in the works, which in their current state include the very controversial 'right to be forgotten' and the right not to be 'profiled' without their consent. If correctly implemented, these reforms could, give users of wearable devices the right to have all their personal data deleted, and could require suppliers in the industry to ask for consent before sending their personal data to be analyzed or for predictions about their work performance, current health, location, behavior or personal preferences. Consent would need to be very specific and actively communicated to the user, so sweeping consents or burying important terms in the fine print may not be enough.
The changes are, however, still being heavily debated, with the goal of being finalized soon. In any case, they could possibly result in ongoing compliance costs for corporations in the wearable device industry.
Ultimately, as is often the case with emerging technologies, it falls to the industry to grapple with these compliance issues. Until the law catches up, device manufacturers, tech vendors and businesses that use or allow employees to use wearables need to address the legal challenges in order to exploit this new technology in a lawful way whilst realizing the potential benefits of wearable technology in business.
Originally posted on Data Science Central
Follow us @IoTCtrl | Join our Community
We went to IoT World last week in Santa Clara, California, where over 150 vendors and 10,000 attendees were showing their wares and making connections. More posts on that soon. In the meantime, here's our third issue of the IoTC Bi-Weekly Digest. If you're interested in being featured, we always welcome your contributions on all things IoT Infrastructure, IoT Application Development, IoT Data and IoT Security, and more. All members can post on IoT Central. Consider contributing today. Our guidelines are here.
Featured Articles
Who's Your Buddy? An interview with Dave McLauchlan, CEO & Co-Founder, Buddy Platform
By David Oro
Last week at IoT World, I stopped by the Buddy Platform booth (namely because of their killer Lego set-up). Buddy provides data hosting and management solutions for manufacturers and vendors of connected ("IoT") devices. Prior to IoT World, I sent Buddy CEO and Co-Founder Dave McLauchlan a few questions. Here's what he had to say.
People talk about the Internet of Things (IoT) but few know what it even means in practice
By Danielle Storey
The technology sector is buzzing with predictions and hype about the Internet of Things (IoT), but many people are still confused about what it means, what the real world opportunities are and why businesses should be looking into IoT.
These Are The Weakest Points in Your IoT Security
By Shayla Price
The Internet of Things is changing the world, heralded as one of the most pivotal technology trends of the modern era. We are getting ready to enter a time where everything, quite literally, is connected to the Internet. For the industrial sector, this is a new area of exploration. Factories have smart infrastructures that use sensors to relay data about machine performance. Cities have smart grids that monitor everything from traffic to the energy used by streetlights. Hospitals can monitor the health of high-risk, at-home patients.
In other words, we are entering a hacker's dream world.
The Internet of Things >> Birth of a tech ecosystem purpose-built for disruptive growth
By Roger Attick
The Internet of Things (IoT) concept promises to improve our lives by embedding billions of cheap purpose-built sensors into devices, objects and structures that surround us (appliances, homes, clothing, wearables, vehicles, buildings, healthcare tech, industrial equipment, manufacturing, etc.). What this means is that billions of sensors, machines and smart devices will simultaneously collect volumes of big data, while processing real-time fast data from almost everything and...almost everyone!!! IoT vision is not net reality Simply stated, the Internet of Things is all about the power of of connections.
Additional Links
Follow us on Twitter | Join our LinkedIn group | Members Only | For Bloggers | Subscribe


